Preparing computers for Distributed MIL
- See also

 Availability
Availability 
 Previous
Previous
- Next

-
Allocate a remote Orion HD system on that computer.
-
Present a display on that computer.
-
Access that computer's file system with current user credentials.
-
The controlling application connects to the remote computer using the default or explicitly specified server connection port.
-
The remote computer spawns a new instance of the Distributed MIL server.
-
The new instance of the Distributed MIL server selects a connection port from the range of specified ports on the remote computer.
-
The remote computer informs the controlling application of the newly selected port.
-
The controlling application disconnects from the remote computer.
-
The controlling application reconnects to the remote computer using the port selected in step 3.
To use Distributed MIL, you must prepare all computers with the appropriate software. All computers that you want to use in a Distributed MIL configuration must have MIL/MIL-Lite installed with the Distributed MIL option selected.
During MIL installation, select the Distributed MIL option from the tree in the MIL optional components pane of the Matrox Imaging Setup dialog box. You will then choose how to start the Distributed MIL server, which is discussed below. Once installation is complete, the Distributed MIL components, including the Distributed MIL server, are installed on the computer, along with MIL/MIL-Lite. You must make sure that all the computers in the cluster have the appropriate licenses.
If exchanging image buffers across the network, it is recommended that the computers have at least a GigE Ethernet interface (1000BaseT).
Setting up the Distributed MIL server on remote computers
A computer must be running the Distributed MIL server to accept new incoming connections and to create new outgoing connections. The Distributed MIL server manages all of a remote computer's connections; the server transparently opens and closes the required connections as necessary.
Distributed MIL typically manages the Distributed MIL server, but you can control when it starts and stops running. In the monitoring configuration, the MIL functions will completely manage the server regardless of any explicit attempts to control it. In the controlling configuration, you must ensure that the server is running on any computer on which you will allocate a DMIL remote system. During installation (and afterwards with the MILConfig utility), you can select to start the server as a service, start the server at logon, or start the server manually. You will typically want to start the Distributed MIL server as a service. This will cause the server to start automatically when you boot the computer, and to recover automatically if the server crashes; you won't need to logon to the computer to start the server.
The Distributed MIL server cannot be running as a service on a remote computer if you plan to:
In these cases, you must select to start the server at logon. To set it to run at logon, open the MILConfig utility and select Run at every logon with user credentials in the Server Settings pane, found under the Distributed MIL item. Then, before a Distributed MIL application can access the computer, you must logon to the computer; once logged on, the server will start automatically.
When developing a distributed application using DMIL, you might need to share files between computers. You can specify an application context on a remote computer as a source or destination for MappFileOperation(); this allows you to easily transfer files between MIL applications with a single function call. You can also use MappFileOperation() to execute a program on the remote computer. For more information see the Working with files section of Chapter 2: Building an application.
Managing network connections and ports
You don't need to manage all the separate connections required between the computers in your cluster. However, you must establish a port on the remote computers to which their Distributed MIL server should listen for new connection requests, and that your application should access to initiate new connections.
By default, the Distributed MIL server listens to port 57010 or 57020 for new connection requests when in the controlling configuration or the monitoring configuration, respectively. If the remote computer uses this port for other purposes, you can specify a different listening port number using the MILConfig utility on this computer. When you specify a non-default port for the server, you should specify that your controlling or monitoring application uses the same port to connect to the remote computer. You can change the default server connection port, which the local computer uses to connect to a remote computer, using the MILConfig utility on the local computer. If some of your remote computers don't use this default port, your controlling or monitoring application must explicitly specify the port to access on these remote computers. For an example of how to allocate a DMIL remote system on a specific port, see the Allocating DMIL remote systems subsection of the Controlling configuration section later in this chapter. For an example of how to connect to a publishing computer on a specific port, see the Monitoring application subsection of the Monitoring configuration section later in this chapter.
Note that your application remains more portable if your application does not explicitly specify the port to access during system allocation.
The connection between computers is typically made using TCP/IP.
It is also possible, but not required, to specify a passkey server side (on the remote computer). This ensures that only MIL applications which specify the passkey during connection are given access. To set up the passkey, specify it in the MILConfig utility on the remote computer in the Server Settings pane; the passkey is a string of up to 16 case-sensitive alphanumeric characters. The controlling/monitoring computer must pass the passkey along with the system name, port, and system type to the remote system(s) or publishing application(s) when establishing a connection to the remote computer(s) using MsysAlloc() or MappOpenConnection() (depending on if you are using a MIL controlling configuration or a MIL monitoring configuration respectively). The remote computer will then validate the authenticity of the passkey which was passed to it from the controlling/monitoring application. Each remote computer in a Distributed MIL application can have a different passkey.
Note that you cannot specify a passkey for a DMIL default system.
Cluster modes and port range
In the controlling configuration, the Distributed MIL server can exist in one of two cluster modes: single or multiple. By default, the server is set to single cluster mode, which specifies that the server will only be connected to a single controlling application. By specifying multiple cluster mode, the server is able to be connected to several independent controlling applications. When specifying how to start the Distributed MIL server, you can choose to start the server as a service in single cluster mode or in multiple cluster mode. You specify the cluster mode in the MILConfig utility.
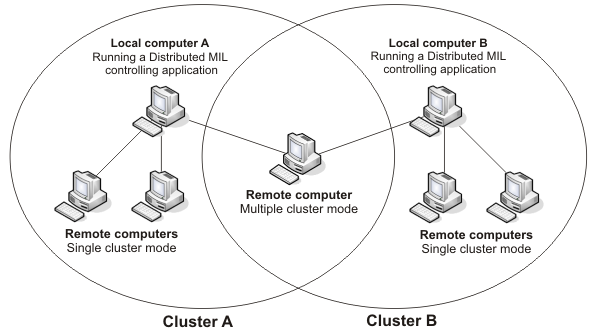
If the Distributed MIL server is in the default single cluster mode, the controlling application connects to the remote computer using the default or explicitly specified server connection port. If the Distributed MIL server is in multiple cluster mode, only the initial connection is made using the default or explicitly specified server connection port. You must establish a range of ports on the remote computer which the Distributed MIL server could use for subsequent connections. You can either use the default range or specify a range using the MILConfig utility on the remote computer. The connection to a remote computer in multiple cluster mode happens as follows:
In this process, the remote computer dynamically selects the port for its connections depending on which ports in its specified range are available; this port management technique allows for the computer to be part of multiple clusters.
When running your application, you can confirm that connections have been set up properly by monitoring the Distributed MIL server's output using the MILConfig utility on the remote computer.
Firewall configuration
When using the TCP/IP communication layer, you will need to ensure that your networking equipment (for example, firewalls and proxy servers) has been configured properly so that it allows Distributed MIL to create all of its required connections.
All computers must be able to accept data from each other on the specified TCP/IP port and port range. When dealing with computers that have Microsoft Windows Firewall enabled, a pop-up will appear during the execution of a MIL application whenever there is a need to use a port blocked by the firewall. Through this pop-up, you can configure the Microsoft Windows Firewall to allow the use of a specific port by a specific application.
To optimize performance for computers behind a Microsoft Windows Firewall, you should unblock these ports using the MILConfig utility. On the Server Settings pane, accessed using the Distributed MIL - Controlling item, select the Microsoft Windows Firewall exception option. Alternatively, you can unblock ports directly using Microsoft Windows by navigating to the Control Panel and adding exceptions to the Microsoft Windows Firewall.
Instead of unblocking the above-mentioned ports, you can disable the firewall for these ports using the Microsoft Windows Firewall interface. Disabling the firewall will stop the firewall software from watching the specified ports. Note that disabling the firewall on specific ports is not recommended if your computers are connected to a large network (such as, the internet).
Licensing considerations
To develop or run a Distributed MIL application, you must have the appropriate licenses:
|
Product |
Mode of operation |
Licenses Required |
|
|
Computers running the controlling, monitoring, or publishing applications |
Computers with DMIL remote systems |
||
|
MIL |
Developing |
MIL development license. |
Runtime licenses for Distributed MIL and any MIL module that the computer actually uses. |
|
Running |
Runtime licenses for Distributed MIL and any MIL module that the computer actually uses. |
||
|
MIL-Lite |
Developing |
Supplemental licenses for Distributed MIL and any other functionality actually used that requires a supplemental license. |
Supplemental licenses for Distributed MIL and any other functionality actually used that requires a supplemental license. |
|
Running |
|||
All computers in the cluster need a Distributed MIL license to either send or receive a DMIL command; a MIL development license includes Distributed MIL. In addition, each computer needs the licenses for any MIL modules/functionality that the computer actually uses. For example, if the controlling application on the local computer calls a Model Finder function using objects allocated on a remote computer, the operation will actually be performed on the remote computer; therefore, only the remote computer needs a Model Finder license.
Note that when all remote computers in a controlling configuration are Matrox computers or smart cameras (for example, Matrox Supersight, Matrox 4Sight GP, and Matrox Iris GTR), the local computer does not need a Distributed MIL license.
For more information on licensing, see Chapter 54: Distribution and licensing.